You're happily browsing your favorite online shop when suddenly the website slows down and then... stops altogether. At first, you might think, "What's wrong with my internet?" but soon you realize that other websites are working just fine. Strange, isn't it? What could be going on?
How do I recognize a DDoS attack?
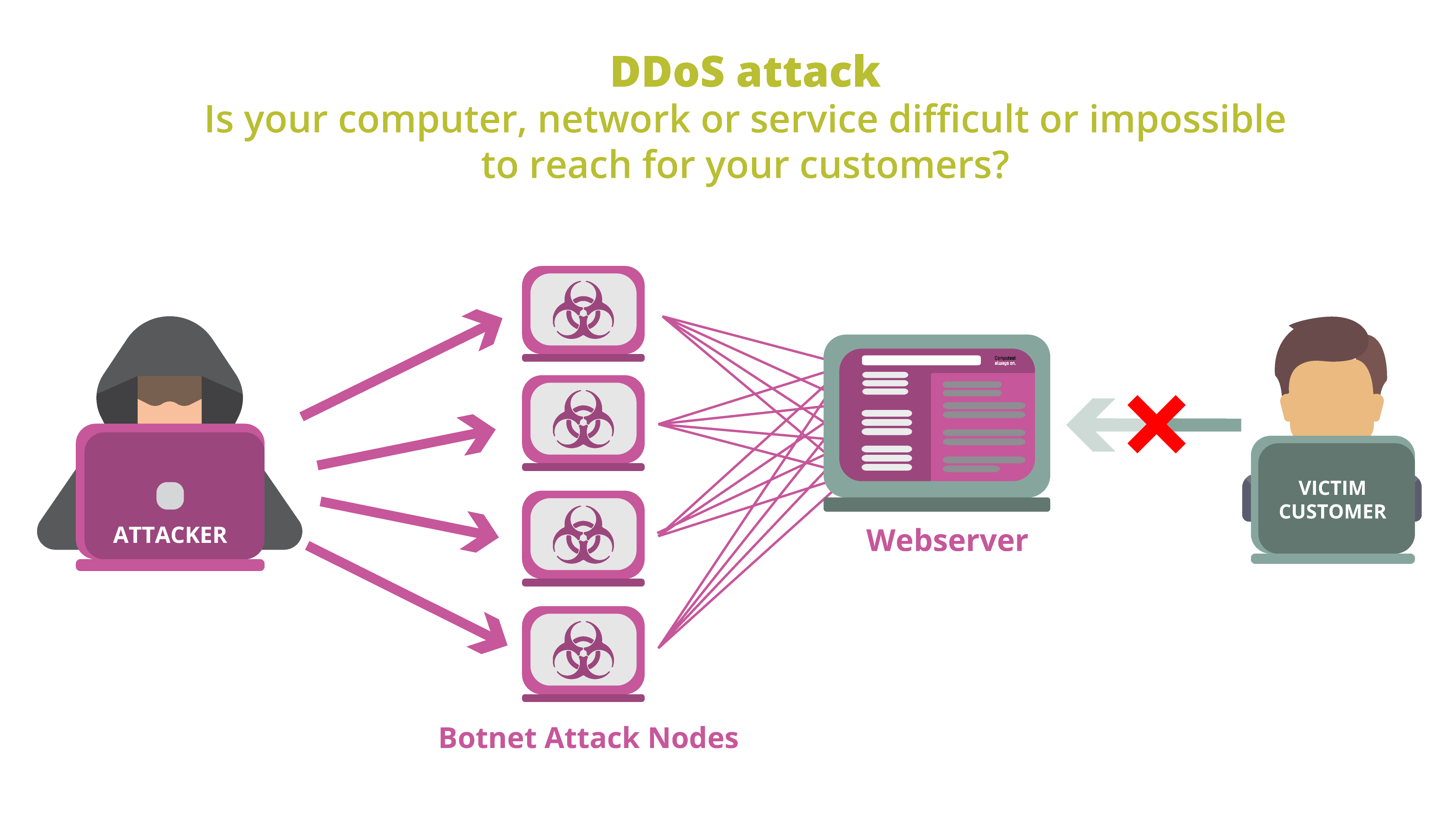
In a Distributed Denial of Service (DDoS) attack, a botnet is often utilized. This is a large network of compromised computers that simultaneously overload the network or server of a webshop or website. The pressure on the network and/or server becomes so immense that you suddenly can't access the website anymore. Quite annoying, especially if your shopping cart is filled with items you want to purchase. Think of it like a traffic jam on the road; when too many cars try to access a road simultaneously, it causes a bottleneck and everything comes to a standstill. The same happens in a DDoS attack. The traffic on the site is so intense that it comes to a halt, and you can't proceed.
Why are DDoS attacks carried out?
Let's delve into the psychology behind a DDoS attack. We categorize the motivations into 1) financial, 2) political, and 3) personal.
- Financial
Sometimes, you might encounter cybercriminals who are after money. When a DDoS attack has a financial motive, it often takes the form of extortion. The criminals put pressure on an organization, typically one that earns its money through online channels, to pay a sum of money. If this doesn't happen, the criminal will initiate a DDoS attack to make this sales channel (either for a prolonged period or in waves) inaccessible. Imagine you own an online shop; your site goes down, and you can't sell anything.
Another motive might be to use DDoS attacks as a diversionary tactic. During a DDoS attack, it's usually not immediately clear why a company is being targeted. Although data theft doesn't often occur right away, it's crucial to find and stop the source of the attack. While you're busy dealing with the DDoS attack, cybercriminals can proceed with other attacks, such as stealing or holding important information for ransom.
- Political
Conflict between states is now increasingly being fought not only on land but also online. Hacktivist groups may also be involved. A DDoS attack can assess the strength of a country's digital defense. It can also temporarily weaken a country's digital infrastructure. Government websites have been taken down in the past.
- Personal motivations for DDoS attacks
Personal motives can also be the driving force behind DDoS attacks. Let's look at some examples.
Example 1: Revenge after a negative experience
An individual might launch a DDoS attack in retaliation against a company with which they've had a negative experience.
Example 2: Competition in online gaming
- Revenge in the gaming world: imagine a gamer feels they unfairly lost to an opponent. This gamer might then initiate a DDoS attack (or order one), causing the opponent or the service they're using to go offline. This gives the gamer an advantage and boosts their ranking in the game.
- Seeking fame: some teenagers carry out DDoS attacks for 'fun and fame,' like taking down a school network.
Example 3: Esteem within the community
Attackers initiate a DDoS attack to gain respect or esteem within their community or to demonstrate their technical skills.
Did you know...
A hacker doesn't even need to set up a botnet themselves? DDoS attacks can be ordered on special websites, sometimes for just a few euros. This makes launching a DDoS attack relatively simple.
Most (and quite effective) DDoS attacks are not very technically complicated. This makes it an attractive tool for everything from innocent pranks to serious attacks by malicious hackers. Read more about the technical side of a DDoS attack.
How resilient is your website against a DDoS attack?
Do you want to know how well your website or application can withstand a DDoS attack? With our DDoS test, we simulate the most common types of attacks, such as: SYN Flood, UDP Flood, DNS amplification attack, Connection Flood, Request Flood, and Slowloris attack, to see if you're ready for a real attack.
Even if you have active DDoS protection mechanisms that have never been 'tested,' we can help in a controlled manner with our simulations.
Want to know more? Check out our DDoS test.

